Hello everyone,
I am Nitin yadav from India with my first ever write up so please ignore my mistakes. So without wasting time let's roll to the bug and how I found it.

So it was my first time hunting on a live website. I was so much excited to hunt on a program let's say site.com(can't disclose as per program rules). I don't know much about the bug types and was new to it. So after 3 or 4 days, my excitement turned into boredom. But then I saw a tweet about recon and searched about recon.
Then I came up with a video on the bug hunter's methodology and after watching that I followed every step shown in the video by Jason Haddix

and got with a subdomain terminal.epm.site.com.

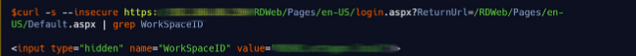
At first, I was like what’s this? And now am totally blank. But I wanted to find a bug so I thought to get the usernames and password for it but can't find it. So I thought of a password spraying attack. So first I need the internal domain name of the target. Which can be found quickly in the RDS login page source as the WorkSpaceId.
Now the challenging part was that I got the internal domain but from where do I get the user list? So for that, i searched about the company on social media if I find something but it was of no use. But I thought of checking LinkedIn and found some names for the company. But the problem was how can I get all the usernames from LinkedIn. Then I remembered about a blog about it and quickly cloned the tool (linkedin2usernames).

Now the structure that the company uses for RD web access was first_last. And the tool does not create this format and from the blog, i got to know about the tool I modified the username list with the tip given there witj sed.
Now its time for some action

Setting up burp intruder for the action-
There are many ways to perform password spraying but Burp suite gives us a considerable amount of flexibility and control. So i started by capturing the login POST request and leaving a placeholder for the username and using the list which i got from Linkdin2username. I launch a attack . But wait it is important to tune this to minimize impact and load on the service.

Launching the Password Spraying Attack
Now its the showtime. And i launched the attack. And after 2 hours i got 302 redirection. And BOOM…… Its what i was thinking about.

Accessing the RDS Service with the Obtained Credentials
I accessed the RD web service using the credentials i got from password spraying attack and the user has a little access but its not what i have concern about.

Without wasting time I reported the bug to company. And within some days i was awarded for that.
- By KD ( Nitin yadav)
Commentaires